
Access Control Systems for Commercial and Residential Buildings
Access control systems help developers, system integrators, and professional installers secure entrances, shared areas, and restricted zones with centrally managed electronic credentials and door control. Compared to mechanical keys, modern electronic access control improves auditability, reduces administrative workload, and scales across single buildings or multi-site portfolios.
On this page you’ll find a practical overview of access control architectures (cloud-based, on-premise, and hybrid), the key system components (readers, controllers, electronic locks, software, and communications), and the most common real-world use cases across offices, residential developments, education, healthcare, industrial sites, and hospitality.
Why this guide is practical
Intertec works with professional access control manufacturers and supports system integrators, installers, and project teams across Europe. This page is written to reflect how access control platforms are typically selected in real projects—based on deployment scale, data control, connectivity, lifecycle maintenance, and integration requirements.
We assist partners with solution selection, system design support, and technical guidance during deployment.
What Is an Access Control System?
An access control system is a security solution that regulates who can enter a building or specific areas within it. Instead of relying on mechanical keys, access control systems use electronic credentials, readers, controllers, and management software to authenticate users and grant or deny access based on predefined rules.
At its core, an access control system consists of door hardware, identification devices, and a centralized platform that manages users, credentials, schedules, and access rights. These systems can operate locally or be managed remotely, depending on the system architecture and project requirements.
Access control systems are designed to improve security, increase operational efficiency, and provide better visibility over building access. They allow organizations to manage access centrally, respond quickly to changes, and scale security infrastructure as buildings or user groups grow. These systems form the foundation of modern building security infrastructures.
Types of Access Control Systems
Access control systems can be implemented using different system architectures depending on project size, infrastructure, and operational requirements. The most common approaches include cloud-based, on-premise, and hybrid access control systems, each offering distinct advantages and limitations.
Cloud-Based Access Control Systems
Cloud-based access control systems are managed through a web-based platform hosted in the cloud. System configuration, user management, and access rights are controlled remotely without the need for local servers on site.
Cloud-based access control is typically selected when:
- Multiple buildings or sites need centralized administration
- Remote user and door management is required
- Fast rollout and easy scaling are priorities
- On-site IT infrastructure should be minimal
Key trade-off: cloud-based systems depend on reliable connectivity and vendor-hosted services, so teams should confirm data governance, uptime practices, and update policies early.
These systems are well suited for projects that require fast deployment, centralized management across multiple locations, and minimal on-site IT infrastructure. Cloud-based access control is commonly used in commercial offices, residential portfolios, and multi-site environments where scalability and remote access are key priorities.
On-Premise Access Control Systems
On-premise access control systems operate using locally installed servers and databases within the building or facility. All system data, configurations, and access rules are managed on site, providing full control over system operation and data storage.
On-premise access control is typically selected when:
- Data must remain fully on site for governance or policy reasons
- Internet connectivity is limited, restricted, or unreliable
- Internal IT/security teams require direct system ownership
- Advanced customization and local control are priorities
Key trade-off: on-premise deployments usually require more on-site IT effort for updates, backups, and long-term platform maintenance.
This architecture is typically chosen for projects with strict data control requirements, limited internet connectivity, or complex security policies. On-premise systems are often deployed in industrial facilities, healthcare environments, and enterprise-level installations where system ownership and local control are essential.
Hybrid Access Control Systems
Hybrid access control systems combine elements of both cloud-based and on-premise architectures. Core system components may operate locally, while management interfaces, reporting, or remote access features are provided through cloud services.
Hybrid access control is typically selected when:
- Projects need a phased transition from legacy systems
- Some functions must stay local while others benefit from cloud access
- Multi-tenant or mixed-use sites require flexible management models
- Teams want a balance between centralized visibility and local continuity
Key trade-off: hybrid designs need clear responsibility boundaries—what runs locally, what is cloud-managed, and how failures are handled.
Hybrid solutions are suitable for projects that require operational flexibility, phased migration from legacy systems, or a balance between centralized management and local system control. They are commonly used in mixed-use developments and large-scale projects with diverse security and operational needs.
Cloud-Based vs On-Premise Access Control Systems Comparison
Project teams typically compare cloud-based and on-premise access control by looking at operational ownership, scalability, connectivity requirements, and lifecycle maintenance. Both models can deliver professional security outcomes—however, they differ in how day-to-day administration, updates, and expansion are handled over time.
Quick rule of thumb: choose cloud-based platforms for multi-site scaling and remote administration; choose on-premise platforms when local ownership, strict data control, or offline continuity is the priority.
| Comparison Criteria | Cloud-Based Access Control | On-Premise Access Control |
|---|---|---|
| System hosting | Hosted in the cloud | Hosted locally on site |
| Deployment speed | Fast deployment with minimal on-site infrastructure | Longer setup due to local servers and configuration |
| Remote management | Full remote access via web-based platform | Typically managed locally or through internal networks |
| IT infrastructure | Minimal on-site IT requirements | Requires local servers and IT resources |
| Scalability | Easily scalable across new doors and multiple sites | Scaling may require additional local hardware |
| Data control | Data stored and managed in the cloud | Full local control over data storage |
| Internet dependency | Requires reliable internet connectivity | Can operate independently of internet access |
| Maintenance and updates | Software updates handled centrally | Updates managed locally by administrators |
| Typical use cases | Commercial offices, residential portfolios, multi-site projects | Industrial sites, healthcare, enterprise environments |
| Preferred by | Organizations prioritizing flexibility and centralized management | Organizations requiring full system ownership and control |
While both architectures support professional access control deployments, the optimal choice depends on operational requirements such as data governance, deployment scale, and long-term system management.
For project teams, the architecture choice impacts long-term operating cost, maintenance workflows, and how easily the system scales across new doors, tenants, or sites.
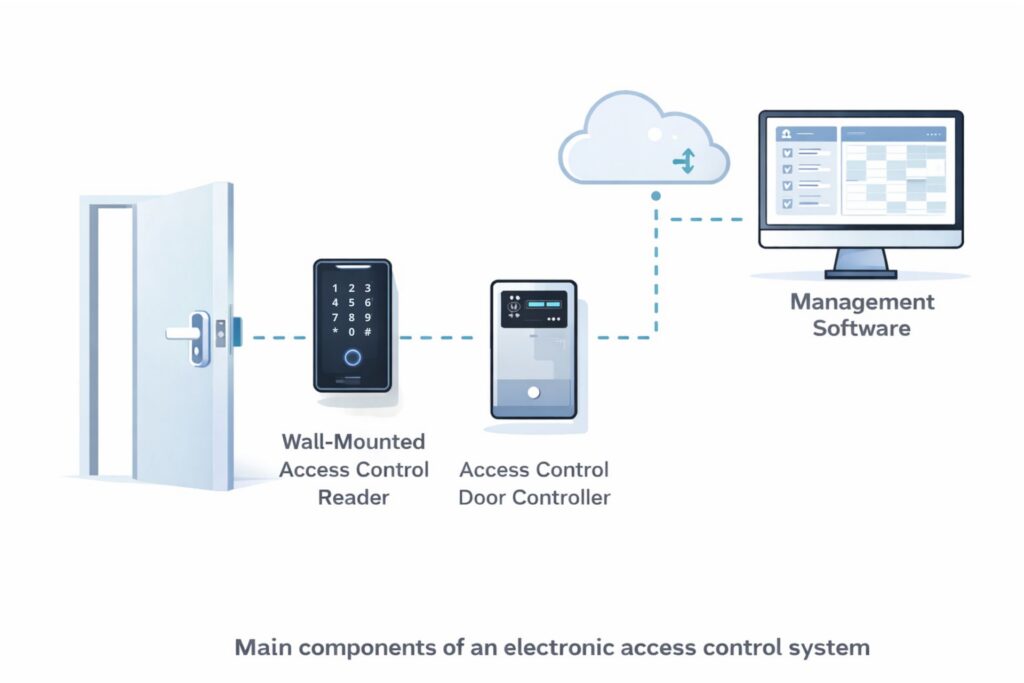
Key Components of an Access Control System
An electronic access control system is built from several core components that work together to authenticate users, make access decisions, and physically secure doors. While system architecture may vary, the fundamental building blocks remain consistent across most access control installations.
Access Control Reader
The wall-mounted access control reader is the primary user interface of the system. It is used to present credentials such as RFID cards, mobile credentials, PIN codes, or biometric identifiers. The reader captures the credential data and sends it to the access control system for verification.
Door Controller
The access control door controller is responsible for processing access requests and enforcing access rules. It receives data from the reader, checks permissions based on system configuration, and triggers door locking or unlocking mechanisms. Controllers operate locally or as part of a networked system, depending on the system architecture.
Electronic Locking Hardware
Electronic locks and door hardware physically secure the door. These components execute access decisions made by the controller, ensuring that doors remain locked or unlocked according to authorized access events, schedules, and security policies.
Management Software
Access control management software provides centralized configuration and monitoring of the system. It allows administrators to manage users, credentials, access schedules, and permissions, as well as review access logs and system events. Depending on the deployment model, management software may be hosted locally or delivered through a cloud-based platform.
Network and Communication Infrastructure
Reliable communication between system components is essential for consistent operation. This includes wired or wireless connections between readers, controllers, and management platforms, as well as secure communication with cloud services when applicable.
For professional installations, component compatibility and secure communication between readers, controllers, and software are critical for reliable operation and future integrations.
Typical Use Cases of Access Control Systems
Access control systems are deployed across a wide range of building types and operational environments. While system requirements vary by project, the following use cases represent the most common and practical applications of electronic access control systems.
Commercial Office Buildings
In commercial office environments, access control systems are used to manage employee and visitor access to entrances, floors, and restricted areas. Centralized access management improves security, simplifies onboarding and offboarding, and enables time-based access rules for different user groups.
Residential and Multi-Unit Developments
Access control systems in residential buildings provide secure and convenient access for residents, property managers, and service providers. These systems are commonly used in apartment complexes, mixed-use developments, and gated communities, supporting features such as shared access points, temporary credentials, and remote access management.
Educational Campuses
Schools, universities, and training facilities use access control systems to secure buildings, classrooms, and staff-only areas. Access control supports controlled entry during operating hours, emergency lockdown procedures, and scalable credential management across large user populations.
Healthcare and Industrial Facilities
In healthcare and industrial environments, access control systems help enforce strict security policies, protect sensitive areas, and ensure compliance with operational and safety requirements. These systems are often integrated with other building security systems and tailored to complex access hierarchies.
Hotels and Hospitality Facilities
Hotels and hospitality environments rely on access control systems to manage guest and staff access to rooms, common areas, and back-of-house spaces. Electronic access control enables flexible credential issuance, improves operational efficiency, and enhances the overall guest experience.
Most projects benefit from mapping user groups, access schedules, and required integrations early—this reduces rework and ensures the platform fits operational realities.
Available Access Control Solutions
Access control solutions are designed to support different system architectures, building types, and operational requirements. Depending on the project scope, access control systems may be deployed as cloud-based, on-premise, or hybrid solutions, using wired or wireless hardware components.
The solutions presented below represent commonly used access control platforms suitable for professional installations in commercial and residential environments.
Cloud-Based Access Control Solutions
Cloud-based access control solutions enable centralized system management through a web-based platform without the need for on-site servers. These solutions are well suited for projects that require scalability, remote administration, and simplified deployment across single or multiple locations.
Typical applications include commercial offices, residential portfolios, and multi-site organizations where flexibility and remote access management are essential.
On-Premise Access Control Solutions
On-premise access control solutions implement locally managed system architectures through dedicated access control platforms installed within the facility. These solutions are designed for projects that require direct system ownership, customized security policies, and full administrative control over access control infrastructure.
On-premise platforms are typically selected for long-term deployments where access control systems are closely integrated with internal IT, security, or building management systems, and where operational continuity must be maintained independently of external cloud services.
Wireless and Electronic Lock-Based Solutions
Wireless and electronic lock-based access control solutions implement access control functionality directly at the door level using electronic locking hardware with integrated readers and local intelligence. These solutions reduce or eliminate the need for extensive door wiring and centralized door controllers.
Such solutions are particularly suitable for retrofit projects, heritage buildings, and installations where cabling is impractical or disruptive. Electronic lock-based platforms are commonly used to extend access control coverage efficiently, support phased deployments, and enable flexible door-by-door system expansion within larger access control infrastructures.
In real projects, the best access control platform is the one that matches how the building will be operated over time. Cloud-based platforms are often chosen for remote administration, fast rollouts, and consistent management across multiple sites. On-premise platforms are typically selected when teams require local control, internal IT alignment, and advanced security policy ownership.
Wireless and electronic lock-based systems are frequently used to expand coverage door-by-door—especially in retrofits, heritage properties, and areas where cabling is impractical. This approach can reduce installation complexity while keeping the access control infrastructure scalable and integration-ready.
Below are professional access control solutions aligned with these deployment models, including a short summary of where each platform fits best.

Access Control Cloud Platform
Cloud-based access control platform enabling centralized management of doors, users, and access rights across single or multi-site buildings. Designed for scalable deployments with simplified administration, remote management, and faster door-by-door expansion over time.
- Cloud-based access control without local servers
- Centralized multi-site administration and visibility
- Scales from single buildings to portfolios
Brand: Salto

Access Control On-Premise Platform
On-premise access control platform providing centralized management of doors, users, and access rights within enterprise and multi-site environments. Built for long-term deployments requiring local system control, advanced configuration, and full administrative ownership.
- Fully on-premise operation without cloud dependency
- Centralized enterprise administration and policy control
- Local database, advanced configuration, and continuity
Brand: Salto
Frequently Asked Questions About Access Control Systems
What is an access control system?
A: An access control system is a security solution that controls who can enter a building or specific areas using electronic credentials instead of mechanical keys. It combines readers, controllers, door hardware, and software to manage access centrally.
What is the difference between cloud-based and on-premise access control systems?
Cloud-based access control is managed through an online platform and enables remote administration across one or multiple sites. On-premise systems operate on local servers on site and provide full control over data storage and system operation.
Which access control system is better for commercial buildings?
It depends on operational requirements. Multi-site commercial buildings often benefit from cloud-based platforms, while facilities with strict IT or data policies may prefer on-premise or hybrid systems.
Are access control systems suitable for residential buildings?
Yes. Access control systems are widely used in apartment buildings and residential complexes to manage entrances, shared areas, and service access using centralized administration and electronic credentials.
When are wireless or electronic lock-based access control systems recommended?
Wireless and electronic lock-based systems are recommended for retrofit projects, heritage buildings, or locations where cabling is impractical. They allow door-by-door deployment with reduced installation complexity.
Can access control systems be integrated with other building systems?
Yes. Professional access control platforms can integrate with video intercoms, alarms, elevators, and building management systems when integrations are planned during system design.
ABOUT
Intertec — authorized distributor of access control systems for installers and integrators.
CONTACT US
Asula 3, 11312 Tallinn
+372 526 2388
info@intertec.ee
Copyright © Intertec OÜ all rights reserved.


